최신 ST0-134 무료덤프 - Symantec EndPoint Protection 12.1 Technical Assessment
What are two criteria that Symantec Insight uses to evaluate binary executables? (Select two.)
정답: A,B
A company is setting up a new environment with three Symantec Endpoint Protection Managers(SEPM) and wants to set one SEPM to act as the primary reporting server. Where in the SEPM should the administrator configure the priority reporting server to be used for running scheduled reports and notifications?
정답: B
Refer to the exhibit.
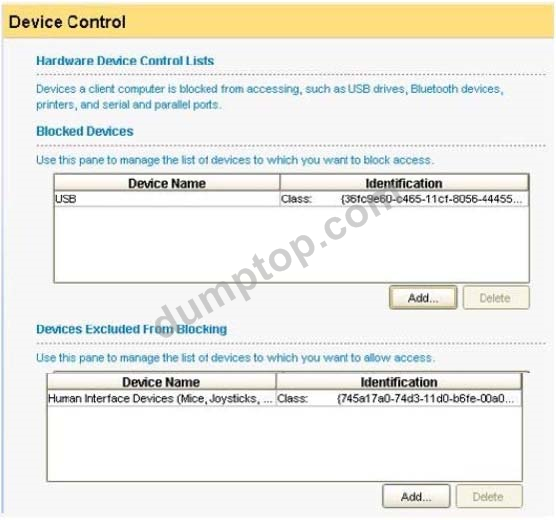
A USB mouse is plugged in to a system that uses the device control displayed in the exhibit. What is the expected behavior?

A USB mouse is plugged in to a system that uses the device control displayed in the exhibit. What is the expected behavior?
정답: C
A user is unknowingly about to connect to a malicious website and download a known threat within a .rar file. All Symantec Endpoint Protection technologies are installed on the client's system. In which feature set order must the threat pass through to successfully infect the system?
정답: C
Which two sources can a Macintosh client use to download content? (Select two.)
정답: A,D
Which feature reduces the impact of Auto-Protect on a virtual client guest operating system?
정답: B
Which port is used by default for replication between sites?
정답: B
A company suffered catastrophic hardware failure on the Symantec Endpoint Protection Manager (SEPM). The administrator restores the hardware and the operating system with the required software (including SEPM). The administrator then runs the SEPM Database Back Up and Restore utility. What is the most important consideration?
정답: C
A Symantec Endpoint Protection (SEP) administrator performed a disaster recovery without a database backup. In which file should the SEP administrator add "scm.agent.groupcreation=true" to enable the automatic creation of client groups?
정답: C
A company has a small number of systems in their Symantec Endpoint Protection Manager (SEPM) group with federal mandates that AntiVirus definitions undergo a two week testing period. After being loaded on the client, the tested virus definitions must remain unchanged on the client systems until the next set of virus definitions have completed testing. All other clients must remain operational on the most recent definition sets. An internal LiveUpdate Server has been considered as too expensive to be a solution for this company. What should be modified on the SEPM to meet this mandate?
정답: B
An administrator is restoring a Microsoft SQL Symantec Endpoint Protection 12.1 database and installing a new Symantec Endpoint Protection Manager (SEPM). After completing the restore, the administrator notices that the clients are unable to connect to the SEPM. Which step did the administrator forget when performing the restore?
정답: B
Which component is required in order to run Symantec Endpoint Protection 12.1 protection technologies?
정답: C
A company is building a new Symantec Endpoint Protection Manager (SEPM) and building email notifications that will go to the security team. Which two notification conditions should the team implement into the SEPM? (Select two.)
정답: A,D
A large enterprise plans to deploy Symantec Endpoint Protection 12.1 (SEP) on 36,000 virtual endpoints distributed across 1,800 VMware ESX servers in a single datacenter. A system administrator needs to optimize endpoint scanning performance by enabling Shared Insight Cache (SIC) server functionality. Which two configuration changes should the administrator make to minimize the number of SIC servers that need to be deployed? (Select two.)
정답: A,C
Where are directory servers added before importing Organizational Units (OU) or adding administrators to the Symantec Endpoint Protection Manager?
정답: A
A company has a firewall policy with a rule that allows all applications on all ports. An administrator needs to modify the policy so that it allows Internet Explorer to communicate to any website, but only on port 80 and 443. In addition, the company only wants this modification to affect traffic from Internet Explorer. The administrator created a new rule at the top of the ruleset that allows Internet Explorer on port 80 and 443. Which step should the administrator take next?
정답: A
According to Symantec best practices, which two tasks should be completed after creating file fingerprint lists, but prior to enabling System Lockdown? (Select two.)
정답: A,B
An administrator enabled virtual image exceptions for Auto-Protect and Administrator-Defined scans on virtual machines. In order to protect against previously undetected threats, the administrator must regularly scan the static instance of the virtual machine image set which includes the files that have been whitelisted. In addition to cleaning the static image set, which additional step must the administrator complete if threats are discovered?
정답: A
